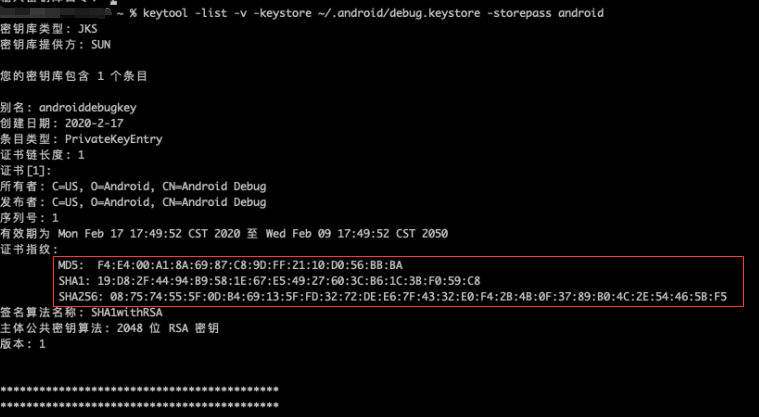
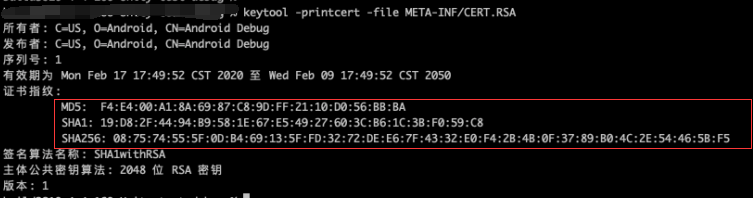
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
| JNIEXPORT jstring JNICALL
Java_com_xie_jun_unitytest_MainActivity_nativeGetCertificateFingerprint(JNIEnv *env, jobject context) {
jclass context_clazz = (*env)->GetObjectClass(env, context);
jmethodID methodID_getPackageManager = (*env)->GetMethodID(env,
context_clazz, "getPackageManager", "()Landroid/content/pm/PackageManager;");
jobject packageManager = (*env)->CallObjectMethod(env, context, methodID_getPackageManager);
jmethodID methodID_getPackageName = (*env)->GetMethodID(env,
context_clazz, "getPackageName", "()Ljava/lang/String;");
jstring packageName = (*env)->CallObjectMethod(env, context, methodID_getPackageName);
const char *str = (*env)->GetStringUTFChars(env, packageName, 0);
__android_log_print(ANDROID_LOG_DEBUG, "JNI", "packageName: %s\n", str);
jclass pm_clazz = (*env)->GetObjectClass(env, packageManager);
jmethodID methodID_getPackageInfo = (*env)->GetMethodID(env,
pm_clazz, "getPackageInfo", "(Ljava/lang/String;I)Landroid/content/pm/PackageInfo;");
int flags = 0x00000040;
jobject packageInfo = (*env)->CallObjectMethod(env,
packageManager, methodID_getPackageInfo, packageName, flags);
jclass packageInfo_clazz = (*env)->GetObjectClass(env, packageInfo);
jfieldID fieldID_signatures = (*env)->GetFieldID(env, packageInfo_clazz,
"signatures", "[Landroid/content/pm/Signature;");
jobjectArray signatures = (*env)->GetObjectField(env, packageInfo, fieldID_signatures);
jobject signature = (*env)->GetObjectArrayElement(env, signatures, 0);
jclass signature_clazz = (*env)->GetObjectClass(env, signature);
jmethodID methodID_toByteArray = (*env)->GetMethodID(env, signature_clazz,
"toByteArray", "()[B");
jbyteArray cert = (*env)->CallObjectMethod(env, signature, methodID_toByteArray);
jclass x509_clazz = (*env)->FindClass(env, "javax/security/cert/X509Certificate");
jmethodID methodID_getInstance = (*env)->GetStaticMethodID(env,
x509_clazz, "getInstance", "([B)Ljavax/security/cert/X509Certificate;");
jobject x509 = (*env)->CallStaticObjectMethod(env, x509_clazz, methodID_getInstance, cert);
jclass md_clazz = (*env)->FindClass(env, "java/security/MessageDigest");
jmethodID methodID_md_getInstance = (*env)->GetStaticMethodID(env,
md_clazz, "getInstance", "(Ljava/lang/String;)Ljava/security/MessageDigest;");
jstring algorithm = (*env)->NewStringUTF(env, "SHA1");
jobject md = (*env)->CallStaticObjectMethod(env,
md_clazz, methodID_md_getInstance, algorithm);
jclass certificate_clazz = (*env)->GetSuperclass(env, x509_clazz);
jmethodID methodID_getEncoded = (*env)->GetMethodID(env,
certificate_clazz, "getEncoded", "()[B");
jbyteArray x509Encoded = (*env)->CallObjectMethod(env, x509, methodID_getEncoded);
jmethodID methodID_digest = (*env)->GetMethodID(env, md_clazz, "digest", "([B)[B");
jbyteArray mdDigestBytes = (*env)->CallObjectMethod(env, md, methodID_digest, x509Encoded);
jclass mainActivity_clazz = (*env)->FindClass(env, "com/xie/jun/checksignaturedemo/MainActivity");
jmethodID methodID_bytesToHexString = (*env)->GetStaticMethodID(env,
mainActivity_clazz, "bytesToHexString", "([B)Ljava/lang/String;");
jstring hexString = (*env)->CallStaticObjectMethod(env,
mainActivity_clazz, methodID_bytesToHexString, mdDigestBytes);
const char *c_hexString = (*env)->GetStringUTFChars(env, hexString, 0);
__android_log_print(ANDROID_LOG_DEBUG, "JNI", "fingerprint: %s\n", c_hexString);
return hexString;
}
|